JWT Assertion
In API Connectivity Manager, you can apply policies to an API Gateway to further enhance their configuration to meet your requirements.
Policies added at the proxy level are applied to all routes within that proxy.
For an overview of the different policy types and available policies, refer to the consult the Learn about Policies topic.
Authentication & authorization policies allow a user to restrict access to their APIs by determining the caller’s identity and access level. There are several API Gateway authentication/authorization policy types supported by API Connectivity Manager: API key authentication, basic authentication, OAuth2 JWT assertion, and OAuth2 token introspection. This guide focuses specifically on OAuth2 JWT Assertion.
JSON Web Tokens (JWTs, pronounced “jots”) are a compact and highly portable means of exchanging identity information. JWTs can be used for client authorization and are a better way to control access to web‑based APIs than traditional API keys. Using JWTs as API keys provides a high‑performance alternative to traditional API keys, combining best‑practice authorization technology with a standards‑based schema for exchanging identity attributes.
API Connectivity Manager API owners can restrict access to their APIs with JWTs. The API Proxy Policy can be configured to grant access to APIs only after validating a client’s JWT.
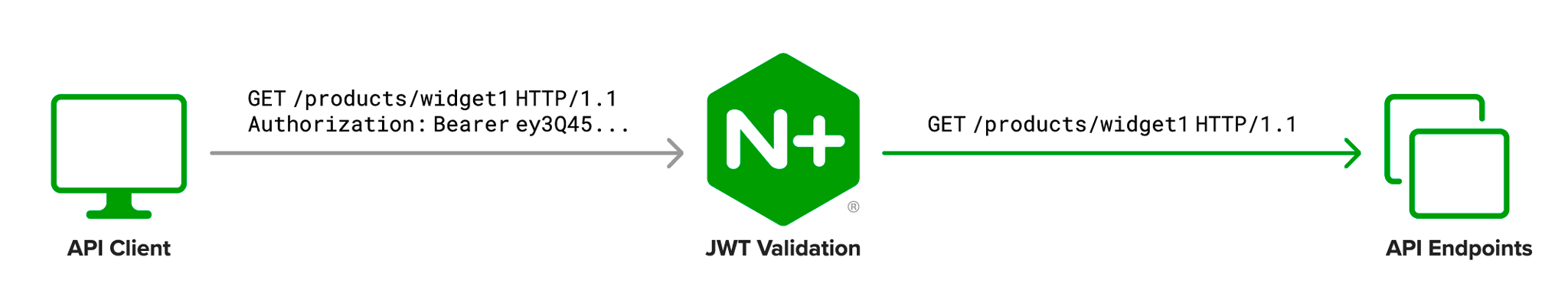
JWTs have three parts: a header, a payload, and a signature. In transmission, they look like the following (line breaks have been added for readability, the actual JWT is a single string):
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.
SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cA period (.) separates the header, payload, and signature. The header and payload are Base64‑encoded JSON objects. The signature is encrypted using the algorithm specified by the alg header, which we can see when we decode our sample JWT:
| Encoded | Decoded | |
|---|---|---|
| Header | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 |
{"alg": "HS256","typ": "JWT"} |
| Payload | eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ= |
{"sub": "1234567890","name": "John Doe","iat": 1516239022} |
The JWT standard defines several signature algorithms. The value HS256 in the example refers to HMAC SHA‑256. F5 NGINX Plus supports the HSxxx, RSxxx, and ESxxx signature algorithms that are defined in the standard. The ability to cryptographically sign JWTs makes them ideal to be used for client authorization.
A JWT is considered to be valid when the following conditions are met:
- The signature can be verified with a local or remote JSON Web Key (matching on the
kid(“key ID”), if present, andalg(“algorithm”) header fields). - The JWT is presented inside the validity period when defined by one or both of the
nbf(“not before”) andexp(“expires”) claims.
Complete the following prerequisites before proceeding with this guide:
- API Connectivity Manager is installed, licensed, and running.
- You have one or more Environments with an API Gateway.
- You have published one or more API Gateways
This guide provides instructions for completing tasks using the API Connectivity Manager user interface (UI).
To access the UI, go to the FQDN of your NGINX Instance Manager host and log in. On the Launchpad menu, select “API Connectivity Manager.”
You can use tools such as curl or Postman to interact with the API Connectivity Manager REST API. The API URL follows the format https://<NMS_FQDN>/api/acm/<API_VERSION> and must include authentication information with each call. For more information about authentication options, please refer to the API Overview.
Take the steps in this section if you would like to restrict access to APIs to clients with a valid JWT. You can set up an OAuth2 JWT Assertion policy using either the web interface or the REST API.
Send a POST request to add the OAuth2 JWT Assertion policy to the API Proxy.
| Method | Endpoint |
|---|---|
POST |
/services/workspaces/<SERVICE_WORKSPACE_NAME>/proxies |
Local JSON Web Key usage with the policy configuration valuejwksKeys[]is recommended for test/debugging environments only. For production environments,jwksURIshould be used for remote JSON Web Key retrieval.
- NGINX Blog: Authenticating API Clients with JWT and NGINX Plus
- [RFC-6749] The OAuth 2.0 Authorization Framework
- [RFC-6750] The OAuth 2.0 Authorization Framework: Bearer Token Usage
- [RFC-7517] JSON Web Key (JWK)
- [RFC-7519] JSON Web Token (JWT)
- [RFC-7521] Assertion Framework for OAuth 2.0 Client Authentication and Authorization Grants
- [RFC-7523] JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants